STEMPLES Plus - Indicators of Change - Hofstede Principles
Learn how to assess your adversary strategically with STEMPLES Plus
Watch Promo
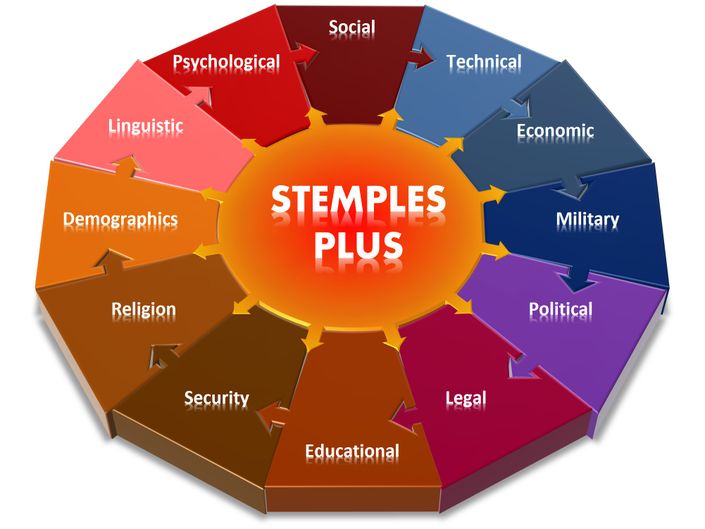
Organizations use the STEMPLES Plus framework as an analytical tool used to identify key drivers of change in the strategic environment of target countries. We use this to measure and analyze repeatable indicators of change that may lead to adverse cyber activity against our clients. STEMPLES Plus analysis includes Social, Technical, Economic, Military, Political, Legal/Legislative, Education, and Security. The Plus represents possible indicators of change including Demographics, Religion, and potentially Psychological aspects of the target country. We also measure various target countries to understand how changes in the strategic environment here may invite malicious activity in the cyber arena.We can and do adjust our target context based upon certain capabilities. For example, we may examine target countries as they relate directly and indirectly to their potential for building, supporting, and executing cyberwarfare actions and operations.Strategic intelligence may not shift and change as much as Tactical or Technical Intelligence. STEMPLES Plus may not show changes for months at a time. Some of the shifts may be more subtle than what is seen in these other areas. We adjust to these subtleties by using indicators of change within each strategic area of STEMPLES Plus. Indicators of change may be added as new indicators are discovered. STEMPLES Plus is normally measured quarterly, but we can apply this strategic technique for monthly assessment.
Your Instructor

Treadstone 71 is a woman and veteran-owned small business exclusively focused on cyber and threat intelligence consulting, services, and training. We are a pure-play intelligence shop.
Training dates and locations here
Since 2002, Treadstone 71 delivers intelligence training, strategic, operational, and tactical intelligence consulting, and research. We provide a seamless extension of your organization efficiently and effectively moving your organization to cyber intelligence program maturity. Our training, established in 2008, follows intelligence community standards as applied to the ever-changing threat environment delivering forecasts and estimates as intelligence intends. From baseline research to adversary targeted advisories and dossiers, Treadstone 71 products align with your intelligence requirements. We do not follow the create once and deliver many model. We contextually tie our products to your needs. Intelligence is our only business.
- We use intuition, structured techniques, and years of experience.
- We supply intelligence based on clearly defined requirements.
- We do not assign five people to do a job only one with experience.
- We do not bid base bones only to change order you to overspending.
We are known for our ability to:
- Anticipate key target or threat activities that are likely to prompt a leadership decision.
- Aid in coordinating, validating, and managing collection requirements, plans, and activities.
- Monitor and report changes in threat dispositions, activities, tactics, capabilities, objectives as related to designated cyber operations warning problem sets.
- Produce timely, fused, all-source cyber operations intelligence and indications and warnings intelligence products (e.g., threat assessments, briefings, intelligence studies, country studies).
- Provide intelligence analysis and support to designated exercises, planning activities, and time-sensitive operations.
- Develop or recommend analytic approaches or solutions to problems and situations for which information is incomplete or no precedent exists.
- Recognize and mitigate deception in reporting and analysis.
Assess intelligence, recommend targets to support operational objectives. - Assess target vulnerabilities and capabilities to determine a course of action.
- Assist in the development of priority information requirements.
- Enable synchronization of intelligence support plans across the supply chain.
- ...and Review and understand organizational leadership objectives and planning guidance non-inclusively.
Course Curriculum

STEMPLES Plus - Indicators of Change - Hofstede Principles
Learn how to assess your adversary strategically with STEMPLES Plus
Watch PromoFrequently Asked Questions
How is this course different from the Certified Threat Intelligence Analyst – Cyber Intelligence Tradecraft Certification course?
We found a need to assist organizations to best understand the strategic functions of intelligence. Although there is some overlap in this course, the course goes into greater depth expanding well beyond traditional IT-type threat intelligence building the foundation for supporting decision-making outside of IT. There is some review for those who have taken previous Treadstone 71 courses but this course is the natural next steps in establishing a resilience, and sustainable cyber threat intelligence program. The course moves the functions and capabilities to a valid corporate asset.
Will the course offer the same types of hands-on exercises that make Treadstone 71 training the gold standard?
We deliver several hands-on exercises complete with templates and examples. Our intent is to send each student back to their corporate environments armed with the knowledge necessary to immediately enhance their existing programs or, start new programs with a foundation rooted in excellence.
|
STRATEGIC ANALYSIS |
ESTIMATIVE AND WARNING ANALYSIS |
|
Data, Information, Knowledge, and Intelligence |
The Role of Warning Intelligence |
|
Knowledge Generation |
Key Warning Factors in Preparations |
|
Explicitly versus Tacit Knowledge |
What Is Warning? |
|
Principles of Knowledge Management |
Intentions versus Capabilities |
|
Monitoring your Business Environment |
The function of Warning Intelligence |
|
Analysis Projects |
Indicators and Indications |
|
Analysis Cycle |
Strategic versus Tactical Warning |
|
Briefing |
What is a Warning? |
|
The Management Brief |
Warning as an Assessment of Probabilities |
|
Starting the Project |
Warning as a Judgment for the Stakeholder |
|
Project Brief Checklist |
Indicator Lists: Compiling Indications |
|
Collection Planning |
Fundamentals of Indications Analysis |
|
Attributes of Sources - Source-Centered Collection Plan |
Compiling Indications |
|
The Collection Plan |
Use of Indicator Lists |
|
Segmentation of Sources |
Extracting Indications Data |
|
Valuation of Sources |
The Nature of Cyber Indicators |
|
Separating Rumor from Fact |
Cyber Indications and Warnings |
|
Using Social Media like a Police Scanner |
The Nature of Cyber Indicators |
|
Monitoring and Verifying |
Importance of Cyber Indicators |
|
Image Verification |
Indications Chronology |
|
Video Verification |
Specifics of the Analytical Method |
|
Using the Crowd |
Presumption of Surprise |
|
Verification Process and Checklists |
Scope of Relevant Information |
|
Verification Tools |
Objectivity and Realism |
|
Intelligence Requirements |
Need to Reach Immediate Conclusions |
|
Prioritization |
Inference, Deduction and Induction |
|
Essential Elements of Information |
Acceptance of New Data |
|
Indicators |
Understanding How the Adversary Thinks |
|
Specific Information Requirements |
Consideration of Various Hypotheses |
|
Glossary and Taxonomy |
How Might they Go to Cyber War? |
|
Mission and Requirements Management |
Order of Cyber Battle Analysis in a Crisis Situation |
|
Tools to Use |
Cyber Order of Battle Methods |
|
Data to Collect |
Analysis of Cyber Mobilization |
|
Iterative and Continuous Feedback Loop |
Recognition of Cyber Buildup |
|
The Data Collection Plan |
Preparation for Cyber Warfare |
|
Executing the Plan |
Key Warning Factors in Preparations |
|
Collection from Friendly or Neutral Sources |
The preoccupation of Leadership / Stakeholders |
|
HUMINT |
Cyber Readiness |
|
Free-flow (Cooperation, rules, benefits, risks & issues, analysis) |
Exercises for Preparation versus Cyber Deployment |
|
Interviewing (Cooperation, rules, benefits, risks & issues, analysis) |
Magnitude and Redundancy of Preparations |
|
Sampling (Cooperation, rules, benefits, risks & issues) |
Cyber Wargaming |
|
Networking (Cooperation, rules, benefits, risks & issues) |
What is a Cyber Wargame |
|
Protecting your Sources |
Why run a Cyber Wargame |
|
Across Cultural Barriers |
Objectives |
|
Collecting from Unsuspecting Sources |
Success Factors |
|
Passive Collection |
Common flow |
|
Elicitation (Cooperation, rules, benefits, risks & issues) |
Common problems in setting up and running |
|
Elicitor - Qualities - Cyber Appearance |
STEMPLES Plus |
|
Collection from Public Domain |
Social, Technical, Economic, Military, Political, Legislative, Educational, Security |
|
Anatomy of OSINT |
Plus (Demographic, Religion, Psychological, catchall) |
|
Spelling, Singular/Plural, Acronyms, Jargon, History, Synonyms, Quasi-Synonyms |
Indicators of Change as Applied to STEMPLES Plus |
|
Applications of OSINT |
The ambiguity of STEMPLES Plus Indicators |
|
OSINT overload - Focus |
A Problem of Perception |
|
Collection from Images |
Considerations in STEMPLES Plus Warning |
|
Picture Analysis |
The Relative Weight of STEMPLES Plus Factors |
|
How to apply Intelligence from Image Collection |
Maintaining your STEMPLES Plus Indicators of Change |
|
When to do so |
Isolating the Critical Facts and Indications |
|
Imagery Intelligence output |
Guidelines for Assessing the Meaning of Evidence |
|
Collection from Things |
Hofstede Principles |
|
Back end collection and analysis |
Hofstede as Applied to STEMPLES Plus |
|
Where to apply the collection |
Adversary Baseball Cards |
|
When and How to apply the collection |
Country, Group, Campaign, Individuals |
|
Collection Outsourcing |
Reconstructing the Adversary's Decision-making Process |
|
Analysis |
Benching marking your adversary |
|
Introduction |
Adversary TTPs |
|
Attributes of strategic analysis |
Adversary Profiling |
|
Collector - Analyst Relationship |
Adversary Supply Chain |
|
Collector-Analyst Differences - Corporate alignment - All as one |
Skills and Education |
|
Strategic Analysis Cycle |
Tools and Their Application |
|
Anatomy of Analysis |
Principal Factors in Timing and Surprise |
|
Where, who, when, why, and how |
Examples of Assessing Timing |
|
Pitfalls |
Warning is Not a Forecast of Imminence |
|
Common pitfalls in analysis |
The Problem of Deception |
|
Bias |
Infrequency and Neglect of Deception |
|
Ethnocentric |
Principles, Techniques and Effectiveness of Deception |
|
Wishful Thinking |
Types of Deception |
|
Status quo |
Countering Deception |
|
Herding |
Judgments and Corporate Policy |
|
Previous Judgments |
Facts Don't “Speak For Themselves’’ |
|
Conventional wisdom |
What Do Top Stakeholders Need, and Want, to Know? |
|
Data and meta data |
Intelligence in Support of Policy? |
|
Data QA |
Assessing Probabilities |
|
Data processing and QC |
Improving Warning Assessments |
|
Data Credibility |
Factors Influencing Judgments and Reporting |
|
Source Validity |
General Warning Principles |
|
Data and Source Relevance |
Most Frequent Impediments to Warning |
|
Scoring Methods |
|
|
Data Preparation |
Appendix A – FORMS |
|
Managing incomplete data |
Key Assumptions |
|
Managing conflicting data |
Indicators / Observables Matrix |
|
Weighing Data |
Threat Situational Awareness |
|
Working with experts - |
Detection Indicators – Threat and Disposition |
|
Data Quantity versus Quality |
Threat Type – Description – Disposition |
|
Misperceiving Events |
Priority Intelligence Requirements – Collection Planning |
|
Premature closing |
Kill Chain Phase |
|
Confusing causality and correlation |
Types of Analysis |
|
Flawed analogies |
Decomposition |
|
Functions and Responsibilities |
Link Analysis |
|
Structured Analytic Techniques |
Pattern Analysis |
|
Link analysis/network charts |
Trend Analysis |
|
Timeline/Chronology |
Technical Baseline |
|
Network Analysis |
Functional Baseline |
|
Brainstorming |
Cultural Baseline |
|
Structured Brainstorming |
Tendency Analysis |
|
Virtual Brainstorming |
Cultural Analysis |
|
Nominal Group Technique |
Anomaly analysis |
|
Starbursting |
Semiotic Analysis |
|
Cross-Impact Matrix |
Anticipatory Analysis |
|
Morphological Analysis |
Volatility Analysis |
|
Quadrant Crunching |
Supply Chain Analysis |
|
Scenario Analysis |
Recomposition |
|
Mechanics of Scenario Analysis |
Synthesis |
|
When and why to plan |
Analyst - Stakeholder Interaction |
|
Success factors |
Uncertainty |
|
Design principles |
Decision-making strategies |
|
Attributes of a good scenario |
Challenges |
|
Flow of a Scenario Exercise |
Moving towards a Trusted Advisor Role |
|
Pitfalls in Scenario Analysis |
Cherry picking |
|
Alternative Futures Analysis |
Yes Manship |
|
Indicators |
Groupthink |
|
Indicators Validator |
Compliance Mandatory - Ethics as Identity |
|
Hypothesis Generation |
Legislation |
|
Formulation and testing |
Scope of compliance and ethics in analysis |
|
Theories, Forecasts |
Code of ethics for strategic analysis |
|
Testing |
Organizing a Strategic Analysis Function |
|
The Multiple Hypotheses Generator |
Getting started |
|
Diagnostic Reasoning |
Structure after strategy |
|
Analysis of Competing Hypotheses |
The right structure enables efficient/effective execution |
|
Argument Mapping |
Centralized versus Decentralized - a comparison |
|
Deception Detection |
Organizing a solid team |
|
Key Assumptions Check |
Design principles |
|
Outside In Thinking |
Functional and behavioral competency building |
|
Pre-Mortem Assessment |
Towards a world-class strategic analysis organization |
|
What If? Analysis |
Five Levels of Strategic Analysis Professionalism |
|
High Impact, Low Probability |
Profile of an analyst |
|
Devil’s Advocacy |
Functional competencies |
|
Force Field Analysis |
Behavioral competencies |
|
Maps |
Measuring competencies - Competency models |
|
Flow charts |
Job descriptions and hiring questions |
|
Frequency charts |
Accountability, Key Activities, Results |
|
Story boards |
|
|
Appendices |
This course teaches students how to think independently and stay away from the low-level tactical approaches we see in daily reports. Strategic, big-picture reviews and assessments that incorporate the social, technical, economic, military, political, legislative, educational, and security, plus demographics, religion, and the psychometric (STEMPLES Plus) aspects of an adversary are lost in today's world of current news posing as intelligence. Lecture, Hands-on, Apprenticeship, in-class exercises, student presentations, analytic products, templates, course material— 60 CPEs.
